My First Blog...
Passively Devoted and Actively Curious what made me write my first blog, finally!
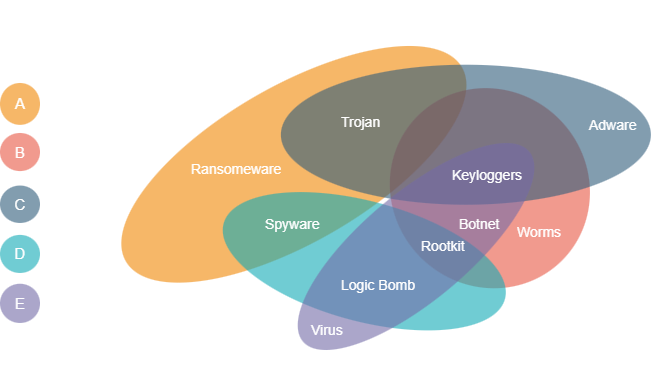
The image somehow helps to depict the picture that runs in my head regarding Malwares. Not a member of the team "bad guys" but fan of those who find such kind of loopholes or create someting so destructive either intentionally or in sake of curiosity, as famously quoted, "Curiosity is the wick in the candle of learning".
I was keen to CyberSecurity the time I started using smartphone, that's in my 7th grade, as a kid it always ignited my mind into thinking how hackers get into such system and demand for money or just block your usage of devices, because in those days I was not into the classification of what's Black hat or Grey hat. The thoughts regarding it matured while pursuing Engineering and then I came across the term "Reverse Engineering", it's like trying to figure out the recipe for someone else's secret sauce. There you caught me, that's the reason I am interested in Malwares, so that by knowing about them I get to the secret receipe of creator. The brain hack behind this and how to secure the system for the next challenge.
Lets's get into the history of Malwares.....
The theoretical foundation for it was drawn in 1966 by John von Neumann, furthermore the actual implementation was done in 1971 "Creeper" by Bob Thomas, it is the first known example of a worm but wasn’t made with malicious intent and didn’t damage or disrupt the systems it infected, instead only displaying the whimsical message: “I’M THE CREEPER : CATCH ME IF YOU CAN.”
This is introductory blog, in upcoming blogs we will visit new forms of Malware and the logic behind them.

